With the demands of a mobile workforce, wireless networks in enterprise environments are quite common. Typically, enterprise wireless networks employ WPA-Enterprise security features, which removes the need for preshared keys (WPA2-PSK) that float around between employees creating security concerns of sharing or unauthorized access upon termination, etc.
These WPA-Enterprise (802.1x) wireless networks often make use of protocols known as Extensible Authentication Protocol (EAP) types. Here is a quick breakdown of commonly seen EAP types including some pros/cons:
- EAP-LEAP - Cisco proprietary using MS-CHAP, considered weak.
- EAP-MD5 - Usernames sent in clear, weak MD5 Challenge/Response prone to cracking.
- EAP-PEAP - Most common EAP type, identity sent in clear, handshake secured via TLS.
- EAP-TLS - End-to-end encryption, secure, administrative burden. Client certificates.
Knowing that a large percentage of enterprise wireless networks deploy EAP types other than EAP-TLS (due to the administrative burden of managing client certificates), we can leverage known weaknesses in EAP types to harvest valuable information. This information can include usernames, certificates, and weak challenge/response hash functions that can be cracked. While these EAP weaknesses are nothing new, I struggled to find a tool to help penetration testers quickly identify EAP types and weaknesses. This is where the idea for crEAP came from.
Introducing crEAP
There are plenty of wireless assessment utilities that exist such as Kismet, Wifite, etc. These all do a great job of identifying WPA-Enterprise mode networks and authentication protocols such as TKIP/CCMP, but do not give details regarding the EAP type. In the past, a tester would have to obtain PCAPs for each network and sift through them to extract useful information. This was a burden on engagements with multiple networks within scope. We sought a utility to help automate identifying WPA EAP types and insecurities. This lead us to the development of crEAP.
Example: airodump-ng displaying CIPHER and AUTH type, but no EAP information.
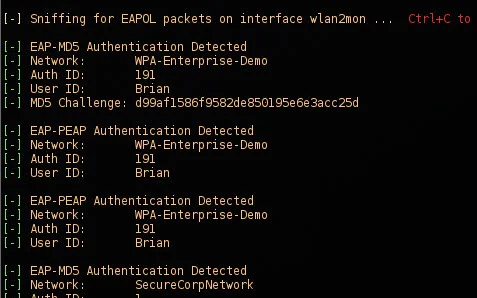
crEAP is a python script that will identify WPA Enterprise mode EAP types and if insecure protocols are in use, will attempt to harvest usernames and/or handshakes. The most commonly deployed EAP types (such as EAP-PEAP) identify users in clear-text by default, which can be gold for a penetration tester looking to harvest employee lists. The crEAP utility attempts to monitor for wireless EAPOL handshakes on the fly and extract data such as usernames and challenge/responses coming over the air. This tool expands on eapmd5crack by running against live captures while adding support for different EAP types (such as PEAP username harvesting).
For EAP-PEAP authentication, once the client identifies, the remainder of the authentication is encrypted via a TLS tunnel. Our simplistic use case is for red or blue teams to run crEAP and passively harvest usernames over the airwaves. This script doesn't attempt to replace the rogue radius server attacks, rather we're interested in simply filling the void of passively identifying EAP types and harvesting users.
Remediation: Some wireless clients offer 'Enable Identify Privacy' under advanced Protected EAP options. This setting provides an anonymous username during the unencrypted phase 1 negotiation of PEAP, then once the TLS tunnel is built, securely identifies with the username. This modification would thwart an attacker's ability to harvest clients that have this enabled.
You can download the crEAP script from Shellntel's Github (here):
git clone https://github.com/Shellntel/scripts.git
Harvesting usernames and challenges from EAP types MD5 and PEAP
Note: After the development of crEAP, I scoured the web and stumbled across a killer tool called EAPeak developed by Spencer McIntyre. His tool does similar actions (plus some) and is worth a look if your into this kind of stuff. Better yet, run them both in tandem.
Happy harvesting!
Travis - @w9hax